Securing funding for healthcare IT projects is no small challenge, but the proper guidance can make all the difference. Discover actionable strategies to simplify the funding process, avoid common pitfalls, and identify opportunities tailored to your organization’s needs. Learn how Global IT partners with healthcare providers to overcome financial barriers and bring innovative IT solutions to life. Don’t miss the chance to unlock the resources you need to drive progress in patient care and operational efficiency—read the full article now.
Legal professionals handle sensitive client data, yet many assume compliance guarantees security. Cyber threats evolve rapidly, exposing firms to breaches that can lead to financial and reputational damage. Regulations set the foundation, but proper protection requires a proactive security strategy. Learn how to strengthen defenses, close security gaps, and safeguard critical legal information with expert guidance from Global IT.
Los Angeles businesses rarely choose security based on technology alone. The real decision is operational: how to reduce downtime, protect sensitive data, and support growth across offices, remote teams, and third-party vendors. Los Angeles cloud security can deliver fast scaling and standardized access—while on-premise security can offer direct custody and predictable boundaries. The best fit depends on accountability, recovery readiness, and how consistently security controls can be maintained month after month.
As the California Privacy Protection Agency (CPPA) prepares its next major round of regulations, the upcoming CPPA 2026 requirements will significantly reshape how organizations collect, govern, and protect personal data. These rules expand on the CPRA, establishing new obligations around transparency, automated decision-making, cybersecurity audits, and data minimization.
Los Angeles healthcare compliance services are now business-critical as enforcement and cyber risk rise in parallel. Recent HIPAA actions—including PIH Health’s $600,000 settlement on April 23, 2025 (phishing, ~189k affected) and Vision Upright MRI’s settlement on May 15, 2025 (unsecured PACS, 21,778 affected)—underline an expectation of proactive, continuously verified controls, not paperwork after incidents.
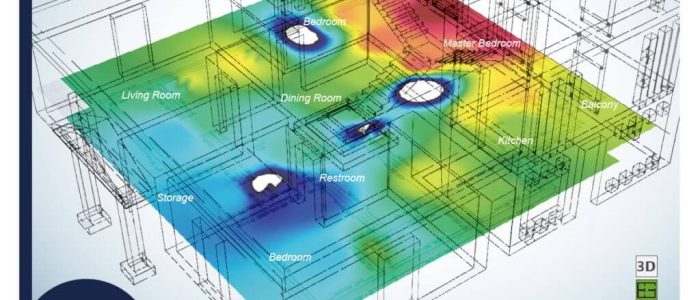
In today’s business world, wireless connectivity isn’t just part of your infrastructure — it defines your performance, productivity, and customer experience. But while companies often invest heavily in access points, routers, and smart devices, they often overlook a foundational diagnostic tool: the wireless heatmap.
In today’s digital landscape, CPA firms in Los Angeles and beyond are managing increasingly complex cybersecurity threats, strict compliance mandates, and the need for seamless collaboration across teams. With financial data being among the most sensitive and regulated, the cost of poor IT infrastructure or a security breach can be catastrophic to a CPA firm’s reputation and operations.
Think cables are just cables? Think again.
From crystal-clear video calls to fast file transfers and secure backups, low-voltage cabling powers the tools your business relies on every day. And yet—it’s often overlooked until there’s a problem.
Let’s pull back the ceiling tiles and see why expertly designed, installed, and managed cabling infrastructure makes all the difference.
In an era where cyber threats evolve daily and public expectations for seamless services are at an all-time high, government agencies face a critical question: How can they modernize operations while safeguarding sensitive data? The answer is increasingly pointing to a specialized, rapidly growing solution — GovCloud. GovCloud is not just another buzzword in the tech world. It represents a secure, compliant, and scalable cloud environment specifically designed for government agencies and organizations handling regulated data.
Strategic Security: More Than Just Cameras Effective security starts with intelligent design. CCTV systems aren’t just for reviewing incidents—they’re for preventing them. From entry points to blind spots, parking lots to server rooms, our security strategies ensure total situational awareness.
At Global IT, we design, install, and support surveillance networks that provide real-time visibility and long-term peace of mind.