Protecting Against Common Computer Threats
 There are two types of common threats most non technical staff will encounter.
There are two types of common threats most non technical staff will encounter.
- “Phishing” for information
- “Viruses” never friendly
- What to do
Phishing
Develop a healthy skepticism when reading any email that asks for sensitive information and take a couple of simple steps to protect you.
- Familiar alarmist messages from ADP, Efax, eBay, Amazon, Facebook or email companies to enter and renew passwords, threats of account closures or documents to open
- zip attachments or any type of attachment
- Promises of money for little or no effort
- Deals that sound too good to be true
- Requests to donate to a charitable organization after a disaster that has been in the news
- Bad grammar and misspellings
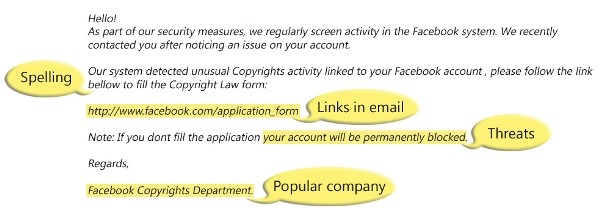
What does a phishing email message look like?
Here is an example of what a phishing scam in an email message might look like.
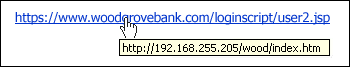
- Beware of links in email. If you see a hyperlink in a suspicious email message, don’t click on it. Roll your mouse (BUT DO NOT CLICK) over the link to see if the address matches the link that was typed in the message. In the example below the link reveals the real web address, as shown in the box with the yellow background. The string of cryptic numbers looks nothing like the company’s web address; be watchful for incorrect domains or spelling for example the real domain is http://linkedin.com, however the hyperlink is linking to http://sign-into-linkedn.com (Notice the “linkedn.com” is incorrect and should be “linkedin.com”).
- If in doubt, retype the URL. When in doubt retype the URL and go to the known website. Phishers are very sophisticated in their use of design and technology to make their email lures look legitimate. The URL for the link in a phishing scam email usually appears to be a company’s valid Web address. If you click the link, you’re redirected to the phishers’ phony sites which look very much like the live site. However, if you type the displayed address into your browser rather than clicking the link, you can avoid being redirected.
- Spelling and bad grammar. Cyber-criminals are not known for their grammar and spelling. Professional companies or organizations usually have a staff of copy editors that will not allow a mass email like this to go out to its users. If you notice mistakes in an email, it might be a scam.
- Spoofing popular websites or companies. Scam artists use graphics in email that appear to be connected to legitimate websites but actually take you to phony scam sites or legitimate-looking pop-up windows.
- When in doubt, throw it out. You can always get a file from someone on paper or on disk. Delete messages with suspect attachments as soon as you can.
Viruses
Viruses are commonly sent as zip attachments or are hyperlinks in emails or web pages.
- If you receive but are not expecting an attachment from a known source delete it.
- Virus attachments often come from Facebook, LinkedIn, YouTube, Amazon, resumes, financial information, contact spreadsheet, American Express etc. Delete these messages immediately.
- Viruses can also be linked and downloaded from hyperlinks offering free iPad’s or other gifts on untrusted websites.
i. Be cautious of known viruses; like speed up your PC/computer or free antivirus and ad-ware removal tools.
ii. In most cases once these viruses are in the system, they go into learning mode to watch and obtain your access information silently.
- Viruses can also be sent as computer updates. Recently attackers have been using fake computer updates to install malicious software on PC.s
i. Be sure to ask your administrator before installing any type of software or software update
What to do
- Delete the email threats immediately, never click on anything that is not certain.
- Make sure your antivirus is active and you are not using a free service downloaded from the web.
- Run a virus scan, and set up an automated weekly scan.
- If you do click on a virus you may not notice any immediate problems until the virus is fully embedded into your system.
i. Press the escape key multiple times and disconnect your computer from the local network or shut it down.
ii. Report it to your technical lead.
iii. Catching and cleaning it early is much better than waiting for the virus to learn your username, password information and then wipe your files or infect other computers.
[authorsure_authors]