 When the world starts to hear about the exploits of a computer virus, it means the virus is performing some serious damage around the world. When ransomware was introduced, it took viruses to a whole new level. Ransomware is a virus that locks up your data files and then demands that you pay a ransom to have those files unlocked. It is difficult to understand how these transactions can take place without the FBI being able to track the offenders, these viruses are causing damage around the business world.
When the world starts to hear about the exploits of a computer virus, it means the virus is performing some serious damage around the world. When ransomware was introduced, it took viruses to a whole new level. Ransomware is a virus that locks up your data files and then demands that you pay a ransom to have those files unlocked. It is difficult to understand how these transactions can take place without the FBI being able to track the offenders, these viruses are causing damage around the business world.
Towards the end of 2014, the ransomware virus named Dridex started attacking banks, and ransoms were being paid to servers in secret locations all over the world. But now it looks like the virus developers are attempting to trap a broader audience as the new ransomware virus called Locky is attacking hospitals, using a method that would work with any type of organization anywhere in the world.
How Does Locky Work?
When Locky was first introduced, it was disguised as a macro on documents using older versions of Microsoft Word. Once a user downloaded the document, the macro would immediately go to work infecting one machine, or an entire network. Newer versions of Microsoft Word do not recognize the macro, so now the virus is delivered in a ZIP file that has to be opened to be activated.
 Once Locky is activated, it immediately creates copies of all of the documents on a server or desktop computer using the extension .locky. These documents are put into an encrypted file and the originals are deleted completely from the system. A ransom message then appears on the screen demanding a payment to a specific Internet address using an online form of payment called bitcoins. If the ransom is paid, a code is sent to unlock the files. If the ransom is not paid, the files are all deleted.
Once Locky is activated, it immediately creates copies of all of the documents on a server or desktop computer using the extension .locky. These documents are put into an encrypted file and the originals are deleted completely from the system. A ransom message then appears on the screen demanding a payment to a specific Internet address using an online form of payment called bitcoins. If the ransom is paid, a code is sent to unlock the files. If the ransom is not paid, the files are all deleted.
One Hospital Fought Back
Locky has been labeled by many security experts as one of the most lucrative ransomware viruses in existence. CryptoWall 3.0 is a ransomware virus that is said to have brought in $325 million dollars in ransoms, and Locky could be on its way to eclipsing that amount very soon. According to ThreatPost.com, experts have been able to detect 3,680 successful deployments of the Locky virus every hour since the virus was released in January. Victims seem powerless to do anything, but one hospital fought back.
One of Locky’s first big victims to publicly talk about their attack was Hollywood Presbyterian Medical Center in Los Angeles, California. Doctors could not use the computer system to treat patients, so they had to fax information back and forth with information providers and other hospitals around the world. The Locky ransom for this attack was initially reported to be $3.6 million. Administrators attempted to work around the virus, but it is alleged that the hospital finally paid $17,000 to get back online.
The Methodist Hospital in Henderson, Kentucky reported that it was hit by Locky and was able to get back online without paying the ransom. How did they do it? The administrators went through each computer one-by-one, including the servers, and scanned for the virus. When the found the virus, they removed it and loaded the backup files. The backup was not as recent as hospital officials would have liked, but the hospital publicly reported that the virus was gone and no ransom was paid.
Protecting Yourself from Locky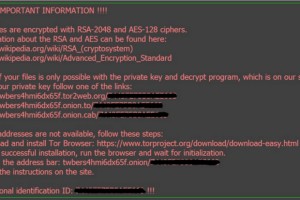
Locky arrives as an attachment to an email, the attachment then needs to be opened for the virus to be distributed. According to Blytheco.com, there are several ways for companies to protect themselves from viruses such as Locky. The first is to make sure you are using quality computer security or anti-virus software, which updates implementations constantly. While updated software may not be able to identify Locky right now, it can detect that there is something wrong with the attachment in the email.
The other way to protect your company from viruses like Locky is to develop a strong email policy that prohibits employees from opening suspect email attachments, and train your IT department to learn how to test attachments for viruses. Many companies have computers not attached to their networks that they use to open suspect attachments they cannot identify. Following these types of steps can help prevent your company from ever having to pay a faceless criminal a ransom for your own data.
For further protection:


