If you have never heard of or experienced ransomware? If not, you can consider yourself very lucky. In this age of growing cyber crimes and online terrorism are on the rise. It is important that everyone know what ransomware is and how to fight it.
Our nation’s critical infrastructure, including both private and public sector networks, are targeted by adversaries. American companies are targeted for trade secrets and other sensitive corporate data, and universities for their cutting-edge research and development. Citizens are targeted by fraudsters and identity thieves, and children are targeted by online predators. –FBI
What Is Ransomware?
The simple answer to defining ransomware is that it is a virus that takes hold of your computer and demands payment to a criminal organization to get the password that will release the virus. This affects personal and corporate computers, and it has become a big business for the criminal world. It is estimated that cyber-ransoms will become a billion dollar industry in 2016, and that only includes the paid ransoms. That figure does not include the costs for repairing the computers or recovering the information.
Once ransomware is downloaded, you will get a message telling you that your computer has been locked and you will be told that you need to take some kind of action to pay the ransom. The consequences of not paying include having all of your data erased, or permanently locking up your computer.
The more complicated description of ransomware is that it preys on your more vulnerable software applications and encrypts your computer. Normally, encryption is used to protect your data. But in this case, it locks you out of your computer and requires a password that only the criminal knows. When you pay the ransom, you hope to get the password that will open up your system. In some cases, the password is not provided after the ransom has been paid.

The FBI doesn’t support paying a ransom in response to a ransomware attack. Paying a ransom doesn’t guarantee an organization that it will get its data back—there have been cases where organizations never got a decryption key after having paid the ransom. Paying a ransom not only emboldens current cyber criminals to target more organizations, it also offers an incentive for other criminals to get involved in this type of illegal activity. And by paying a ransom, an organization might inadvertently be funding other illicit activity associated with criminals.-FBIHow do you get Ransomware?
In corporate settings, ransomware usually arrives in an employee’s email account as what looks like a safe and secure attachment. But when the attachment is open, the ransomware is loaded and it may start to move its way through the rest of the network.
In any setting, email is the most common way that ransomware gets loaded onto a computer. The second most common way is clicking on an infected website and having it loaded directly onto your computer. As frustrating as these can be, these delivery methods give us clues on how to combat these attacks.
Avoiding Ransomware
Always use a reputable antivirus software vendor and can scan your received emails and warn you against websites that are infected. Never use a free AV. You should always have good antivirus operating on your computer, and you should keep your antivirus updated constantly. Corporate IT directors should keep their firewall software up to date, and have a policy in place that prohibits employees from opening email attachments.
Never open an email attachment from a sender you do not recognize. Many of these criminals try to disguise their emails as being from legitimate banks or communications providers, but you should never fall for it. One way to tell if an email is from your bank is to hover your mouse pointer over any link in the email and read the associated link at the bottom of the browser. If the link does not come from your bank, then the email is a phishing email that is looking for victims.
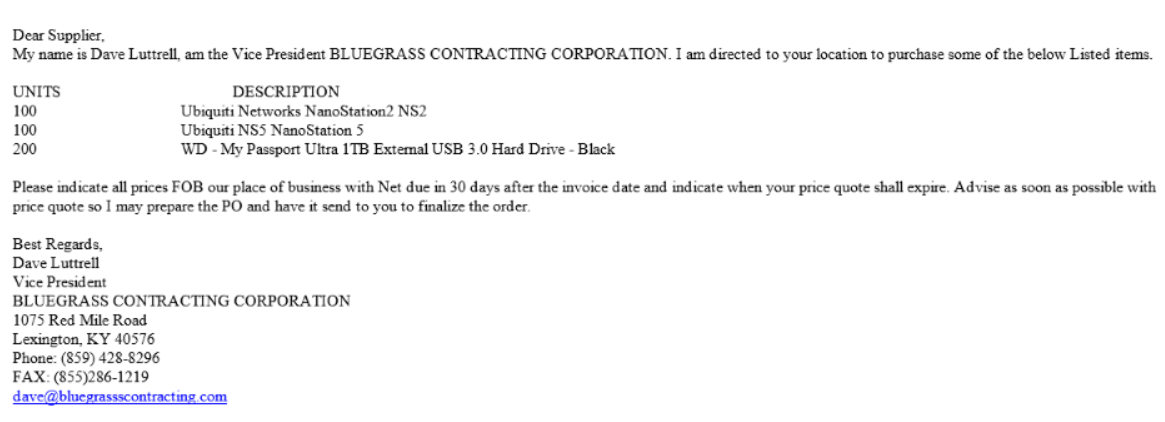
Make sure you look over the data in the email carefully. If you are not familiar with the vendor or the prospective client, call the phone number listed in the email. Here is an example of a fraudulent company that looks legitimate. If you look closely, you can see that there are (3) s’ in the email address dave@bluegrassscontracting.com. This is easy to miss.
Corporate and personal users should always have their computers backed-up to a resource that is not online. For example, personal users can get a large capacity USB drive and back their computers up to that drive every Friday. Corporate users can utilize offline back-up systems that are constantly updated with any changes to the network in case of an attack.
What To Do If You Have Been Attacked
If you open an attachment in your corporate email account and you get the ransomware warning page, then contact your manager immediately. If your manager is not available, then contact the IT manager directly and alert the trusted IT group to the problem.
If you get ransomware on your personal computer, then you should call a computer support professional immediately. Do not try to take care of the problem yourself because it could become worse.
Ransomware is just one of the growing threats that honest Internet users face every day. By practicing safe computer use habits, you can reduce your chances of getting attacked and have yourself covered in case you need to have your hard drive reloaded.




